In today's connected world, sharing data with suppliers is a given. But not all data, and all suppliers, are created equal. Organizations must assess their data-sharing priorities and connect with suppliers that are able to protect the data accordingly. Effective data security must be a critical element in supplier selection, onboarding, and relationship management.
The new CAPS report Digital Connectivity and Data Protection in Supply Management (members only) features a review of best practices and insights from interviews with supply professionals from a dozen large organizations in a range of industries.
In the previous post, we explored some of the risks and tensions organizations face in sharing data with suppliers. These vulnerabilities will inevitably increase as companies and products become connected throughout the supply chain.
As supply management becomes more complex and strategic, supplier data protection is an emerging priority. Supply professionals can apply best practices from other management areas to manage shared data, emphasizing policies, processes, and training.
Now, we'll look at some best practices maintaining data security revealed in the research.
Data Sharing and Protection Decision Cycle
Develop the business case. Internal champions should present a case for the need to share types of data for specific purposes.
Needs assessment. Finalize the business case with internal stakeholders.
Data criticality. Assess the risk of sharing data with varying levels of impact on the organization.
Qualify suppliers. Evaluate suppliers to meet minimum security requirements.
Select suppliers. Identify qualified suppliers to move forward with negotiations.
Contract negotiation. Data security should be incorporated into the contract, including terms of remediation. Plan for data ownership, storage and management during and at the conclusion of the relationship.
Onboarding. Offer security training for data being shared.
Ongoing management. Audit suppliers to assess data sharing, usage, and protections, including penetration testing. Leverage suppliers' knowledge in data security.
Reassessment, renegotiation, and renewal. During the lifecycle and at the end of the contract, assess performance relative to data security and emerging sharing needs.
Sharing and Protection Decision Cycle
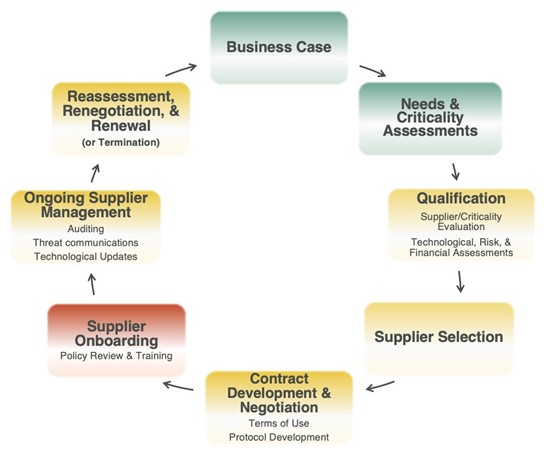
Red = inadequately performed and/or omitted by most companies.
Yellow = some areas for improvement exist (ignoring companies that omitted the stage).
Green = generally performed well (by those companies that performed this step), given practical resource constraints.
Tips for improving data security
Key findings from the research and interviews with leading companies highlighted these steps to improving data security performance.
- Monitor suppliers' compliance with data protection criteria as part of overall assessments
- Add data protection to supply chain and financial risk evaluations
- Develop a playbook for data breach response
- Segment suppliers by the risk of sharing data
- Perform make-buy analysis for third-party security evaluations
- Conduct penetration testing of suppliers' networks
- Track data security performance quarterly to update data sharing needs and industry standards
- Evaluate areas for improvement, as many security assessments are pass/fail
Researchers found many companies have rarely gone beyond surface-level interest in suppliers' vigilance. The research found a lack of auditing or verification of suppliers' claims for their security qualifications during selection. There’s a similar lack of follow-through on monitoring the efficacy of supplier's data protection efforts.
Companies undergo thousands of cyber attacks per day, but there have been few actual breaches revealed so far. Because the bad actors continually probe defenses, organizations and their suppliers mustn’t become complacent in their protection efforts.
Members get priority access
Digital Connectivity in the CAPS Library
Read about the risks, rewards, and tensions in sharing data with suppliers, from our digital connectivity research. CAPS members can access Digital Connectivity and Data Protection in Supply Management in the CAPS Library now. Check out the quick preview video to learn more about the research.
Reports released within the last seven years are reserved for members, but anyone may create a free account in the CAPS Library and access more than 30 years of KPIs, best practices, and thought leadership. Employees of CAPS member companies can access the full report in the CAPS Library now.
Members, download the report Learn more about CAPS membership
Non-members can receive the report of each survey they submit.
Members can access all reports, but are encouraged to submit surveys to
increase the comparative breakouts only they receive.